Shamoon I: A Case Study of Cyber Attacks on Critical Infrastructure in the Gulf
By Camille Capelle
Cyberspace has created the perfect theatre for espionage, covert operations, and asymmetric warfare. Recent trends in the Middle East have revealed a particular focus on cyber-attacks on critical infrastructures, often by state-aligned actors, thus having a significant impact on the geopolitical dynamics of the region. In August 2012, an exceptionally destructive and flashy virus was released on Saudi Aramco, irreversibly wiping the hard drives of 30,000-35,000 computers in the company.[1] While the production line was not affected or any people harmed, the financial impact of the attack due to the interruption of payment systems and distribution records was enormous.[2] This article argues that while the release of the Shamoon virus was not the most physically destructive, nor the most sophisticated cyber-attack, it presented a turning point in cyberwarfare and the general code of conduct of state actors in cyberspace. The use of the Shamoon virus was a distinct move away from the subtle espionage and strategic sabotage operations designed to go undetected, opting instead for dramatic demonstrations of power and technological capability. The dawn of this new type of cyber operation has altered the geopolitical dynamics of conflict in the Gulf, the wider Middle East, and the world.
Even though many people often still associate cyber conflict with mutual state espionage and AI weapons, one of the more dangerous implications are attacks on critical infrastructure. Comprising anything from water treatment plants to the energy sector (production and distribution). The real-life spill over of these digital attacks can cause serious damage, especially in the Middle East where supplies of clean water and temperature control are dependent on industrial processes with high reliance on networked technologies. Here, cyber-attacks have exhibited a particular focus on the energy resource industries such as the oil and gas sectors.[3] While these effects can be inconvenient at best, in the Middle East region they can be catastrophic and even cause loss of life: “It has the highest likelihood of a catastrophic cyberattack of any region in the world, and deadly malware targeting safety systems has not appeared anywhere else.”[4]
Ever since the discovery of the Stuxnet virus and the physical damage it caused to the equipment used for uranium enrichment in the Iranian nuclear facility in Natanz, the physical damage which malicious software is capable of inflicting has shocked the world. While Iran today is often blamed for a variety of cyber-attacks in the Middle East, Europe, and the US, it has primarily been a target for cyber-attacks itself. In the early 2000s and 2010s, Iran was the target of the famous Stuxnet virus, as well as other espionage and Wiper viruses which targeted its oil sector. Iran’s history being the frequent victim of offensive cyber-attacks has prompted its own investment into both defensive and offensive cyber capabilities as these incidents highlighted the need for an effective defence as well as a weapon with which to strike back. On top of this, Iran has been able to learn from the code of the malware used in attacks against it, and partially replicated them for its own offensive uses, as seen in Shamoon. Striking similarities in malware analysis are one of the criteria by which cyber-attacks can be attributed to specific actors.
A CLOSER LOOK AT VIRUS AND ITS USE:
On the 15th of August 2012, a destructive virus was activated inside the networked computers of the Saudi Arabian Oil Company. The suspicious malware had been spreading and installing itself weeks beforehand, lying in wait for its hard-programmed start date and time. The activation date for the attack strategically coincided with the religious holiday, to give the virus maximum time to spread and inflict damage while employees were out of the office. The Shamoon virus, also known as W32.Disttrack, is a destructive virus intended to irrecoverably damage core data on computers, rendering them inoperable. It does this by selecting key files and folders, listing them, and then proceeding wipe each one and then overwrite them, making them much harder if not impossible to recover. It then replaces key files with the picture of a burning American flag which emerges on the screen.
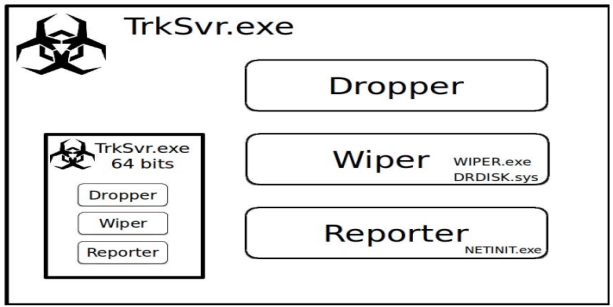
The virus also overwrites the Master Boot Record (MBR) of each infected computer, preventing the device from restarting at all and the hard drive becomes permanently damaged.[5]
The malicious software has three different components: the Dropper, which installs the malware and other key components as well as triggering the attack; the Wiper, which executes the listing, wiping, and overwriting of key files and data, including essential programming of the computer itself; and the Reporter, which sent back live data about the attack including the list of wiper files, allowing the engineers of the attack to follow its development closely.[6] To spread between computers, the virus also stole user credentials. None of these elements are exceedingly sophisticated but, in this case, they did not need to be. Once inside the system, the surprise and unexpected destructiveness of the virus did the rest. The replacement of files with the image of a burning American flag would have had a higher shock factor if there hadn’t been a bug in the code which prevented all but the first line of pixels to load onto the screen. Subsequent versions of Shamoon used in 2016 and 2018 resolved this bug but replaced the image with a more horrific one: the infamous photograph of the body of the drowned three-year-old Syrian boy, washed up on a beach in Bodrum, Turkey. The important psychological element of these cyber-attacks is more than clear.
The virus got its name from one of the folders identified by cybersecurity analysts which the malware loaded itself onto called Shamoon.[7] Conflicting reports have emerged about how the malware was suspected to be delivered to the company’s network. A common tactic is the installation of malware through phishing emails, but some analysts are arguing for a simple USB delivery by a someone on the inside. In-depth analysis by several cyber security companies has revealed that the code for Shamoon was very similar to the American-Israeli Wiper virus unleashed on an Iranian oil company just months before. Fears of Iran’s capacity to learn from cyber-attacks against it were already expressed by the US officials in a leaked NSA document published on the Intercept. Now, these fears have come to life as Iran uses the same adapted tools to strike back against the US and its allies.
THE PROBLEM OF ATTRIBUTION OF CYBER-ATTACKS:
One of the most significant challenges of cyber-attacks is the problem of attribution. Whether perpetrated by cybercriminals or a state-sponsored hacker group, knowing where the attack is coming from is essential to reaction, retaliation, and future prevention. While suspicions and convincing theories always arise, international law holds very high standards to establish attribution, including evidence for a great level of direct state involvement.[8] Although this is necessary to prevent certain manipulations of conflicts to provoke escalation, it also makes legitimate retaliation by victims almost unattainable. Until the 2012 cyber-attack on Saudi Aramco however, most states limited their operations to subtle sabotage and long-term espionage intended to remain undetected and therefore avoid consequences. The Shamoon virus however, with its high visibility, marked a distinct difference. In this instance plausible deniability over the attack provided enough to hide behind to avoid repercussions.
Attribution of cyber-attacks is usually based on two main factors, sophistication, and similarity to other attacks. The sophistication criterion assumes that states with highly developed technology industries will have more sophisticated cyber-weapons, and that state actors in turn, due to their budget and resources, will have more sophisticated cyber-weapons than non-state actors. However, the factor remains problematic for assessment due to the lack of definition when it comes to what “sophisticated” malware is. In the case of Shamoon, while it may have been labelled a highly sophisticated attack by government officials, one of the leading cybersecurity companies Kaspersky Lab dubbed it the Shamoon virus “quick and dirty.”[9] The virus did however include a considerable resemblance to the Wiper virus used in an attack against Iran the same year.
Iran particularly has a paradoxical relationship with the attribution of cyber-attacks. In the wake of the Stuxnet incident on Iran’s nuclear facility in Natanz, Iran has invested heavily in its cyber capabilities and today is one of the countries in the region with the highest number of certified cyber professionals in the region. Due to its isolation from the international community and technological aid, Iran has been forced to develop an independent ‘homegrown’ cyber industry. Since then, Iran has been loudly praising and publicizing its offensive cyber capabilities, while rejecting responsibility for operations linked to it.[10]
However, in the case of the first Shamoon attack, two different previously unknown groups came forward to claim responsibility for the attack, highlighting that even confession doesn’t always establish clear responsibility. Eventually the first group, the Cutting Sword of Justice, released a series of stolen company IP addresses from the hack which were verified as legitimate by the Saudi Aramco. The group cited their motives as opposition to Saudi crimes in the region. The group was subsequently linked to the Iranian government.
While the responsibility of Iran for the Shamoon virus cannot be considered an established fact, for the purpose of this essay, this assumption can be made based on the evidence mentioned above. Nevertheless, theories of attribution should always be approached critically. The problem of attribution has also led to a change in the dynamics of deterrence, since retaliation is no longer a guarantee, and the stakes are difficult to measure.
IMPACTS ON CONFLICT IN THE MIDDLE EAST:
Cybersecurity analysts and scholars have identified the impact of the Shamoon attack on Saudi Aramco as primarily financial. While the exact losses for the company are difficult to estimate, another more significant impact were the repercussions on tensions and conflict in the region. What makes the attack on this oil company so significant is that Saudi Aramco is entirely owned by Saudi leaders who have used this wealth to maintain their economic and political influence in the country. Therefore, an attack on Saudi Aramco is not just an attack on a commercial industry, but on the Saudi state itself.
The Shamoon virus represents a shift in the use of cyber weapons in the Middle East, moving from subtle but sophisticated state attacks to more ostentatious flashy attacks executed by state-aligned hacker groups or actors instead of state agencies themselves. This distancing of responsibility from the state itself has allowed for virus to become less sneaky, as actors count on the attribution problem for protection from serious retaliation instead. From this moment onwards, we see many more openly offensive cyber-attacks in the region, particularly from states with less developed cyber capabilities. The incident therefore marks a rise in state-sponsored hacking, altering the appearance of cyber threats for states and companies alike. The focus of activities on critical infrastructures, particularly on the oil and gas industries is also steadily on the rise.
The dawn of cyber weapons in interstate conflicts has altered the way states pursue their strategic goals abroad. Since cyber weapons are considerably cheaper to develop than conventional weapons, isolated countries like Iran have shown a particular preference for their use. This way, Iran is able “to strike at adversaries globally, instantaneously, and on a sustained basis, and to potentially achieve strategic effects that it cannot in the physical domain.”[11] Adding to this the lack of accountability that cyber-attacks invite into existing conflicts, they have become a way to exhibit hard power without direct consequences. [12]
Since the initial Shamoon attack on Saudi Aramco in 2012, the virus has been adapted and implemented two more times, in 2016 and 2018, to target Saudi key industrial sectors as well as government agencies. Despite reusing 90% of the initial malware’s code, the virus remained effective and more refined with each use, highlighting Saudi Arabia’s continuing vulnerability to this kind of cyber-attacks.[13]
CONCLUSION:
The emergence of cyber-attacks on critical infrastructure as an increasingly common tool has changed the face of regional and international conflicts in Middle East. The use of cyber-weapons is a way to wreak cheap havoc on regional conflicts, especially in a region where geopolitics have proven to be so volatile.[14] Recent trends have shown that the cyber threat to countries in the Gulf, and the wider Middle East, is ever-present and continuously growing as state and non-state actors become more technologically capable. As a result, cyberspace has become a central theatre for the cold conflict between Iran and Saudi Arabia and the other Arab Gulf states. Having clearly understood the importance and destructive potential of cyber-attacks, Gulf states have invested heavily in their cyber defence and attempted to foster a domestic cyber capability to mitigate these dangers, but the threat is far from over. Similarly, a recent article from the news agency Arab News revealed Saudi Arabia had been the victim of 7 million cyber-attacks in 2021 alone.[15]Only in July 2021, Saudi Aramco experienced a significant data leak which hackers attempted to use to try to extort $50 million from the company.[16]
“Even as the Iranian attacks failed as a tool of signaling, they revealed a great deal about the continuing evolution of cyber operations. They marked the opening of a new chapter in the developing story of cyber attacks, one in which states beyond top-tier powers like the United States or Russia began deploying these new kinds of capabilities for their own use. More significantly, the Iranian attacks introduced the new phenomenon of cyber attacks designed to be noticed, even if these early examples were not terribly effective as signals. They showed that attacks of this sort could cause damage and yet not prompt retaliation.”[17]
Cyberspace has become an important political tool in both domestic as well as foreign politics, as can be seen by espionage efforts on dissidents at home and abroad, and the manipulation of social media during the Arab Spring.[18]Apart from the rise of digital authoritarianism, cyberspace has become an important frontline in regional conflict, most visible in Iran’s cold war with US allies in the Middle East.
The views expressed in this article are the author’s own, and may not reflect the opinions of the Sciences Po Cybersecurity Association.
Image source: https://fossbytes.com/second-shamoon-2-malware-virtual-machines/
[1] Salem Alelyani and Hashmir Kumar, ‘Overview of Cyberattack on Saudi Organizations’, in Journal of Information Security and Cybercrimes Research 1:1 (June 2018), p. 44.
[2] Ijeoma Onyeji, Morgan Bazilian and Chris Bronk, ‘Cyber Security and Critical Energy Infrastructure’, in The Electricity Journal 27:2 (2014), p. 54.
[3] Blake Clayton and Adam Segal, ‘Energy Brief: Addressing Cyber Threats on Oil and Gas Suppliers’, Council on Foreign Relations (June 2013), pp. 2-3.
[4] Selena Larson and Sergio Caltagirone, ‘Industrial Cyberattacks in the Middle East and International Consequences’, in Michael Sexton and Eliza Campbell (eds), Cyber War & Cyber Peace in the Middle East (Washington, 2020), p. 38.
[5] Christopher Bronk and Eneken Tikk-Ringas, ‘Hack or Attack? Shamoon and the Evolution of Cyber Conflict’ (2013), p. 17.
[6] Sami Zhioua, ‘The Middle East under Malware Attack Dissecting Cyber Weapons’, in IEEE Conference on Distributed Computing Systems (July 2013), pp. 14-15.
[7] Ben Buchanan, The Hacker and the State: Cyber Attacks and the New Normal of Geopolitics (Cambridge, MA, 2020), p. 149.
[8] Clement Guitton and Elaine Korzak, ‘The Sophistication Criterion for Attribution: Identifying the Perpetrators of Cyber-Attacks’, in The RUSI Journal 158:4, p. 67.
[9] Ibid., p. 63.
[10] Collin Anderson and Karim Sadjadpour, Iran’s Cyber Threat: Espionage, Sabotage, and Revenge (Washington, 2019), p. 5.
[11] Michael Eisenstadt, ‘Cyber: Iran’s Weapon of Choice’, The Cipher Brief, 29 January 2017, https://www.washingtoninstitute.org/policy-analysis/cyber-irans-weapon-choice {accessed 04 October 2021}.
[12] Martina Knopova and Eva Knopova, ‘The Third World War? In the Cyberspace. Cyber Warfare in the Middle East’, in Acta Informatica Pragensia 3:1 (2014), p. 30.
[13] Rawan Abdulaziz Al-Mulhim, Lama Adnan Al-Zamil and Fay Mohammed Al-Dossary, ‘Cyber attacks on Saudi Arabia Environment’ in International Journal of Computer Networks and Communications Security 8:3 (March 2020), p. 28.
[14] Kristina Kausch, ‘Cheap Havoc: How Cyber-Geopolitics Will Destabilize the Middle East’, The German Marshall Fund of the United States, 24 November 2017, https://www.gmfus.org/news/cheap-havoc-how-cyber-geopolitics-will-destabilize-middle-east {accessed 1 October 2021}.
[15] Ruba Obiad, ‘Saudi Arabia had 7 million cyberattacks in 2021, Arab News, 26 March 2021, https://www.arabnews.com/node/1832526/saudi-arabia {accessed 1 October 2021}.
[16] David Wethe, ‘Saudi Aramco Confirms Data Leak After Reported Cyber Ransom’, Bloomberg, 21 July 2021, https://www.bloomberg.com/news/articles/2021-07-21/saudi-aramco-confirms-data-leak-after-reported-cyber-extortion {accessed 1 October 2021}.
[17] Buchanan, The Hacker and the State, p. 166.
[18] Kaush, ‘Cheap Havoc’.
Bibliography:
Alelyani, Salem and Kumar, Hashmir, ‘Overview of Cyberattack on Saudi Organizations’, in Journal of Information Security and Cybercrimes Research 1:1 (June 2018), pp. 42-50.
Al-Mulhim, Rawan Abdulaziz, Al-Zamil, Lama Adnan and Al-Dossary, Fay Mohammed, ‘Cyber attacks on Saudi Arabia Environment’ in International Journal of Computer Networks and Communications Security 8:3 (March 2020), pp. 26-31.
Anderson, Collin and Sadjadpour, Karim, Iran’s Cyber Threat: Espionage, Sabotage, and Revenge (Washington, 2019).
Bronk, Christopher and Tikk-Ringas, Eneken, ‘Hack or Attack? Shamoon and the Evolution of Cyber Conflict’, (2013), pp. 1-30.
Buchanan, Ben, The Hacker and the State: Cyber Attacks and the New Normal of Geopolitics (Cambridge, MA, 2020).
Clayton, Blake and Segal, Adam, ‘Energy Brief: Addressing Cyber Threats on Oil and Gas Suppliers’, Council on Foreign Relations (June 2013), pp. 1-9.
Eisenstadt, Michael, ‘Cyber: Iran’s Weapon of Choice’, The Cipher Brief, 29 January 2017, https://www.washingtoninstitute.org/policy-analysis/cyber-irans-weapon-choice {accessed 04 October 2021}.
Guitton, Clement and Korzak, Elaine, ‘The Sophistication Criterion for Attribution: Identifying the Perpetrators of Cyber-Attacks’, in The RUSI Journal 158:4, pp. 62-68.
Kausch, Kristina, ‘Cheap Havoc: How Cyber-Geopolitics Will Destabilize the Middle East’, The German Marshall Fund of the United States, 24 November 2017, https://www.gmfus.org/news/cheap-havoc-how-cyber-geopolitics-will-destabilize-middle-east {accessed 1 October 2021}.
Knopova, Martina and Knopova, Eva, ‘The Third World War? In the Cyberspace. Cyber Warfare in the Middle East’, in Acta Informatica Pragensia 3:1 (2014), pp. 23-32.
Larson, Selena and Caltagirone, Sergio, ‘Industrial Cyberattacks in the Middle East and International Consequences’, in Michael Sexton and Eliza Campbell (eds), Cyber War & Cyber Peace in the Middle East (Washington, 2020), pp. 37-55.
Obiad, Ruba, ‘Saudi Arabia had 7 million cyberattacks in 2021, Arab News, 26 March 2021, https://www.arabnews.com/node/1832526/saudi-arabia {accessed 1 October 2021}.
Onyeji, Ijeoma, Bazilian, Morgan and Bronk, Chris, ‘Cyber Security and Critical Energy Infrastructure’, in The Electricity Journal 27:2 (2014), pp. 52-60.
Wethe, David, ‘Saudi Aramco Confirms Data Leak After Reported Cyber Ransom’, Bloomberg, 21 July 2021, https://www.bloomberg.com/news/articles/2021-07-21/saudi-aramco-confirms-data-leak-after-reported-cyber-extortion{accessed 1 October 2021}.
Zhioua, Sami, ‘The Middle East under Malware Attack Dissecting Cyber Weapons’, in IEEE Conference on Distributed Computing Systems (July 2013), pp. 11-16.
