
By: Nikhita Nainwal
One of the most widely shared videos on social media in 2022 was that of an out-of-control self-driving Tesla in China ramming into pedestrians at full speed. While investigations are still underway, the video has reignited the concerns of the public regarding the safety of autonomous vehicles, which seem to be increasingly adopted around the world. These concerns regarding manufacturing standards and unintentional accidents have often overshadowed the high susceptibility of these vehicles to intentional cyberattacks due to their heavy reliance on modern complex technology. As autonomous vehicles are soon set to become the norm, it is important to understand what cybersecurity implications this would have.
AUTONOMOUS VEHICLES: THE FUTURE OF MOBILITY
Vehicle manufacturers have been tinkering with the idea of self-driving vehicles since the 1920s, but have only since the 1990s been successfully able to develop semi-autonomous vehicles. Autonomous vehicles have already been widely implemented in industries such as mining. Now that the technology has been refined further, direct consumers are more open to owning autonomous vehicles. The demand for such vehicles stems from the fact that such vehicles have more efficient fuel use compared to traditional vehicles, making them more environmentally friendly, additionally, autonomous vehicles are safer than conventional vehicles as they reduce the element of human error in driving. With major players such as Google, Tesla, BMW, and General Motors heavily investing in this industry, it is projected that the market share for automated vehicles will reach US$196.97 billion by 2030 and 54.2 million of such vehicles would have been produced by 2024.
It is important to note that autonomous vehicles may not be fully automatic: and there are five levels of autonomy, with level 1 being mostly under the control of the human driver, and 5 being free from any human control over the vehicle. Most automated vehicles today operate below level 4 due to legal requirements. However, governments around the world are planning their smart cities around the assumption that autonomous vehicles would operate on level 5 in the future.
Autonomous vehicles are made up of a collection of autonomous technologies serving different purposes. Perception technology is used to detect other vehicles, pedestrians, and traffic signals. Cameras and computer vision technology are able to detect patterns and colors. RADAR, LIDAR, and V2X are the sensor components of the car. Driver data and simulation technologies are used to train the algorithm of the system. Localization capabilities are more accurate than standard GPS devices. Thus, such a heavy reliance on technology opens up multiple avenues for a possible cyberattack.
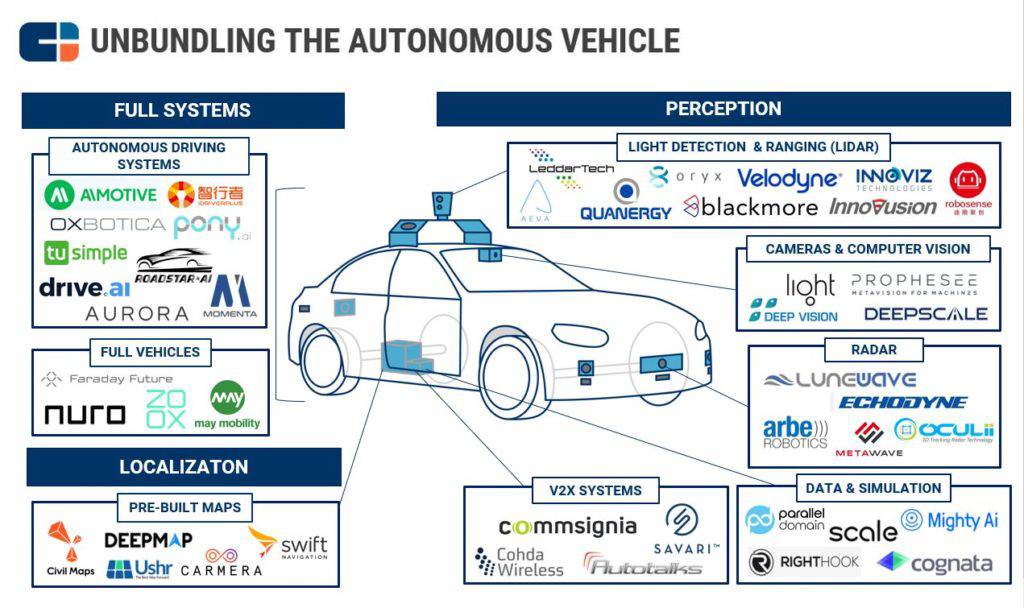
CYBER RISKS OF AUTOMATED VEHICLES
The following are some cyber risks associated with automated vehicles:
- Theft of personal data: These vehicles collect personal information about the user for authentication and communication, just as any other internet service does. This information can range from things such as the owner’s name and home address to their entertainment preferences. This information, in addition to location data, can be used for malicious purposes such as to commit identity fraud or to gain access to the victim’s banking services. Advanced vehicles collect even more sensitive biometric data for voice, face, and fingerprint analysis.
- Theft of vehicle: Most automated vehicles can be unlocked in three ways- NFC card, key fob, and phone application. A security researcher examined Tesla’s unlocking system and found a vulnerability- the use of NFC cards allowed the users to not only unlock the vehicle, but also accept entirely new keys without any authentication. While the phone application is the most frequently used and most secure mechanism for unlocking, adversaries can use a signal jammer to block the frequency used by Tesla’s phone app, forcing the victim to use their NFC card instead, and giving the attacker the opportunity to add any keys they want to the system without the need for authentication. Another security researcher managed to use a relay attack and hardware worth $100 to unlock a Tesla Model 3 with a distance of 15 yards between the attacker and the key fob/phone app.
- Remote control/sabotage of vehicle: There are multiple ways to hack an autonomous vehicle’s systems and technical layers- remote access via the internet or via Bluetooth, inserting a backdoor during a supply chain attack, planting a device onto the vehicle, or modifying the sensory capabilities of the vehicles. These attacks can be used to harm safety-critical functions. DoS attacks, in particular, are dangerous because they can be used to stop camera and sensor functions, which puts the passengers in danger. It can also be used to cause malfunction of the brakes of the vehicle. If an adversary, such as a terrorist, is able to enlist multiple vehicles into a botnet or is able to hack the cloud service, it can lead to mass destruction and death.
- Risk to connected networks: Autonomous vehicles can communicate with several entities. As smart cities get more connected, an infected or compromised autonomous vehicle can spread its malware to other connected entities such as roadside sensor networks, traffic control devices, or electricity infrastructure.
- Ransomware: An attacker can remotely block the user’s access to the vehicle and place ransomware in the system, demanding payment in exchange for access to the vehicle’s functions or to decrypt the data.
RISK MITIGATION
The biggest risk associated with autonomous vehicles emerges from the newness and lack of widespread information about these vehicles. There is a misconception that autonomous vehicles require minimum human attention due to their technical superiority when the opposite might be true. The addition of so many technological layers requires that the user is able to keep track of the security of all the features of their vehicle and is aware of the various vulnerabilities associated with these features. Therefore, it might be a good idea to introduce modified ‘driving tests’ for users of autonomous vehicles. Also, it must be made mandatory for users to undergo regular maintenance and patching of their vehicles as a vulnerable system affects not only the user but also other drivers around them.
Government transport agencies and highway safety agencies, along with private vehicle companies, need to create a data-sharing mechanism to track incidents related to autonomous vehicles. This can help companies manage technical risks and can help authorities understand how to adapt regulations. As autonomous vehicles become increasingly adopted by the public, governments need to invest more in the security of their own systems and understand how these vehicles can impact public facilities such as traffic lights and roadside sensors. Governments can also consider designating certain cities as “autonomous vehicles-only zones”. This makes it easier to study what the consequences of a larger-scale implementation of such a model in real life would be.
Just like any other technology, autonomous vehicles are prone to cyber-attacks. What elevates this risk is the fact that cyber attacks on such vehicles directly endanger the lives of the users and other third parties. Despite the various problems associated with autonomous vehicles, people are still purchasing and using them in large numbers as the perceived benefits of owning them outweigh the perceived costs. Therefore, as the adoption of autonomous vehicles in the future is inevitable, we need to ensure that they are secure enough before they are mass adopted. Education and regulation can help mitigate the cyber risks associated with autonomous vehicles.
The views in the present article are the author’s own, and may not represent the opinions of the SciencesPo Cybersecurity Association.
Image source: https://valientemott.com/auto-collisions/self-driving-cars-pros-and-cons/
References:
CB Insights (2018) Unbundling the autonomous vehicle, CB Insights Research. CB Insights. Available at: https://www.cbinsights.com/research/startups-drive-auto-industry-disruption/ (Accessed: December 2, 2022).
Eliot, L. (2021) Here’s how ransomware is going to fiendishly impede AI self-driving cars, Forbes. Forbes Magazine. Available at: https://www.forbes.com/sites/lanceeliot/2021/06/14/heres-how-ransomware-is-going-to-fiendishly-impede-ai-self-driving-cars/?sh=3c76553b7b63 (Accessed: December 2, 2022).
Goodin, D. (2022) Gone in 130 seconds: New Tesla Hack gives thieves their own personal key, Ars Technica. Available at: https://arstechnica.com/information-technology/2022/06/hackers-out-to-steal-a-tesla-can-create-their-very-own-personal-key/ (Accessed: December 2, 2022).
How can automated and connected cars improve road safety? (2019) RoadSafetyFacts. Available at: https://roadsafetyfacts.eu/how-can-automated-and-connected-vehicles-improve-road-safety/ (Accessed: December 2, 2022).
Igini, M. (2022) Environmental pros and cons of self-driving cars, Earth.Org. Available at: https://earth.org/pros-and-cons-of-self-driving-cars/#:~:text=The%20highly%20advanced%20computers%20controlling,and%20overall%20air%20pollution%20generated. (Accessed: December 2, 2022).
Monteagudo, J. (2022) Cyber security for connected and Autonomous Vehicles, The Cyber Startup Observatory. Available at: https://cyberstartupobservatory.com/cyber-security-connected-autonomous-vehicles/ (Accessed: December 2, 2022).
Murphy, M. (2022) Tesla Hacker proves a way of unlocking doors, starting engine, Bloomberg. Bloomberg. Available at: https://www.bloomberg.com/news/articles/2022-05-16/hacker-shows-off-a-way-to-unlock-tesla-models-start-the-engine (Accessed: December 2, 2022).
On the emerging risks of automation: The case for autonomous vehicles (2022) Swiss Re. Swiss Re Institute. Available at: https://www.swissre.com/institute/research/topics-and-risk-dialogues/digital-business-model-and-cyber-risk/autonomous-mobility-emerging-risks-of-automation.html (Accessed: December 2, 2022).
Placek, M. (2021) Projected number of autonomous cars worldwide, Statista. Available at: https://www.statista.com/statistics/1230664/projected-number-autonomous-cars-worldwide/ (Accessed: December 2, 2022).
Strategic Market Research. (2022) Autonomous car market size to reach $196.97 billion by 2030; CAGR: 25.7% – confirms strategic market research, GlobeNewswire News Room. STRATEGIC MARKET RESEARCH LLP. Available at: https://www.globenewswire.com/en/news-release/2022/10/10/2531178/0/en/Autonomous-Car-Market-Size-to-Reach-196-97-Billion-by-2030-CAGR-25-7-Confirms-Strategic-Market-Research.html#:~:text=10%2C%202022%20(GLOBE%20NEWSWIRE),places%20without%20any%20human%20operator. (Accessed: December 2, 2022).
Truong, J. (2021) How to hack self-driving cars: Vulnerabilities in Autonomous Vehicles, HackerNoon. Available at: https://hackernoon.com/how-to-hack-self-driving-cars-vulnerabilities-in-autonomous-vehicles-jh3r37cz (Accessed: December 2, 2022).
